Enforcing Role-Based Access Control with Attribute-Based Cryptography for Environments with Multi-Level Security Requirements | Semantic Scholar
Virginia State University Policies Manual Title: Personnel Security Policy Policy: 6325 Revision Date: October 3, 2017
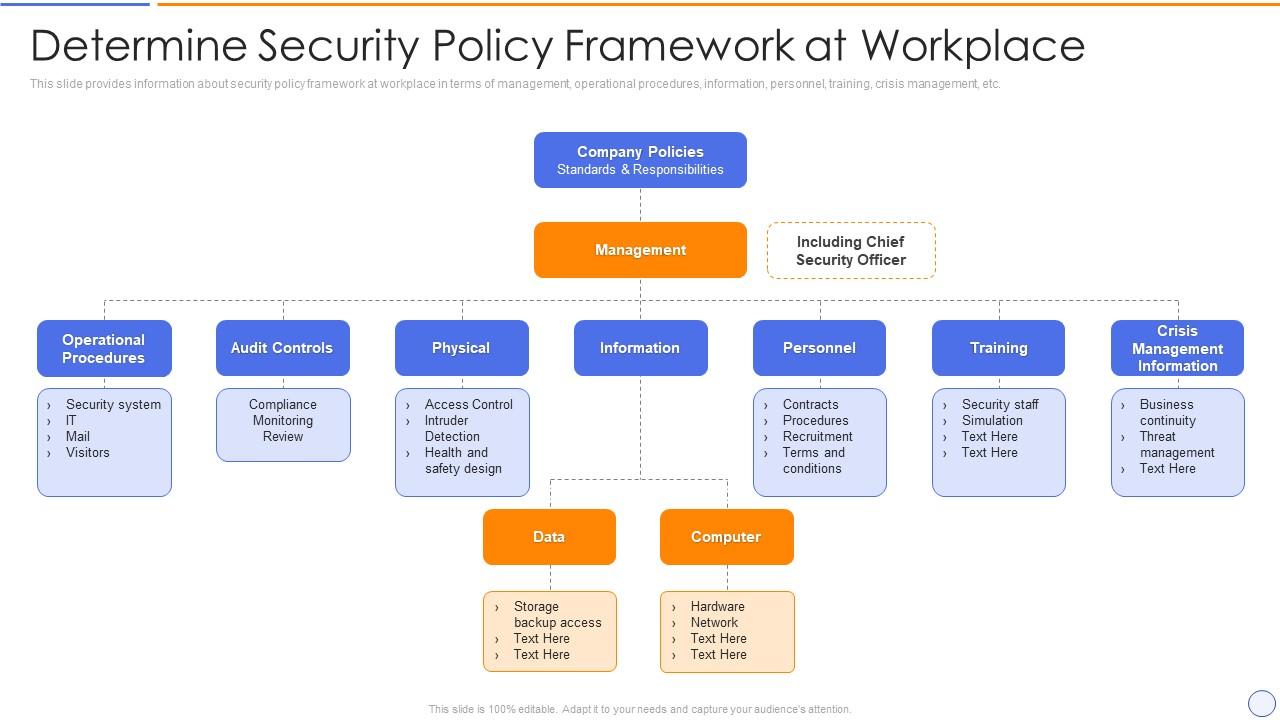
Building Organizational Security Strategy Plan Determine Security Policy Framework At Workplace | Presentation Graphics | Presentation PowerPoint Example | Slide Templates



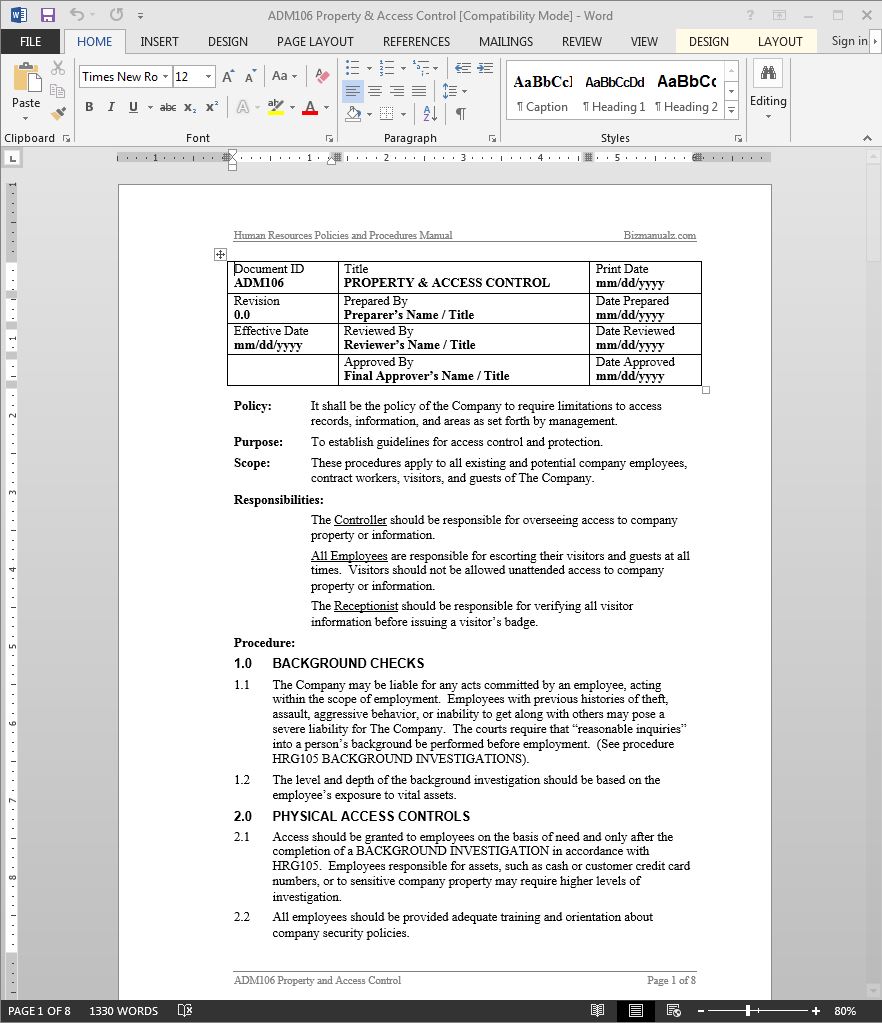



![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab 42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-37.jpg)