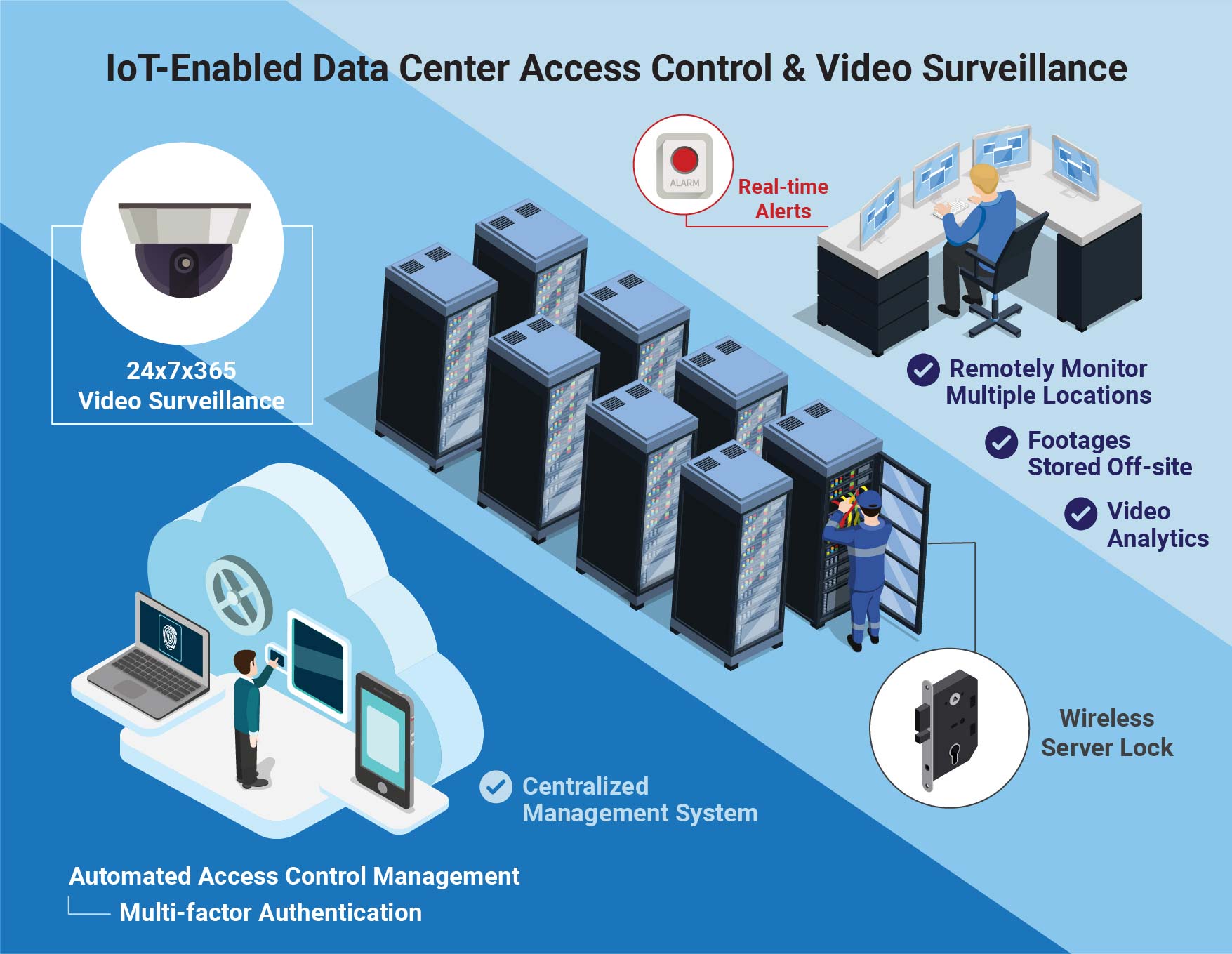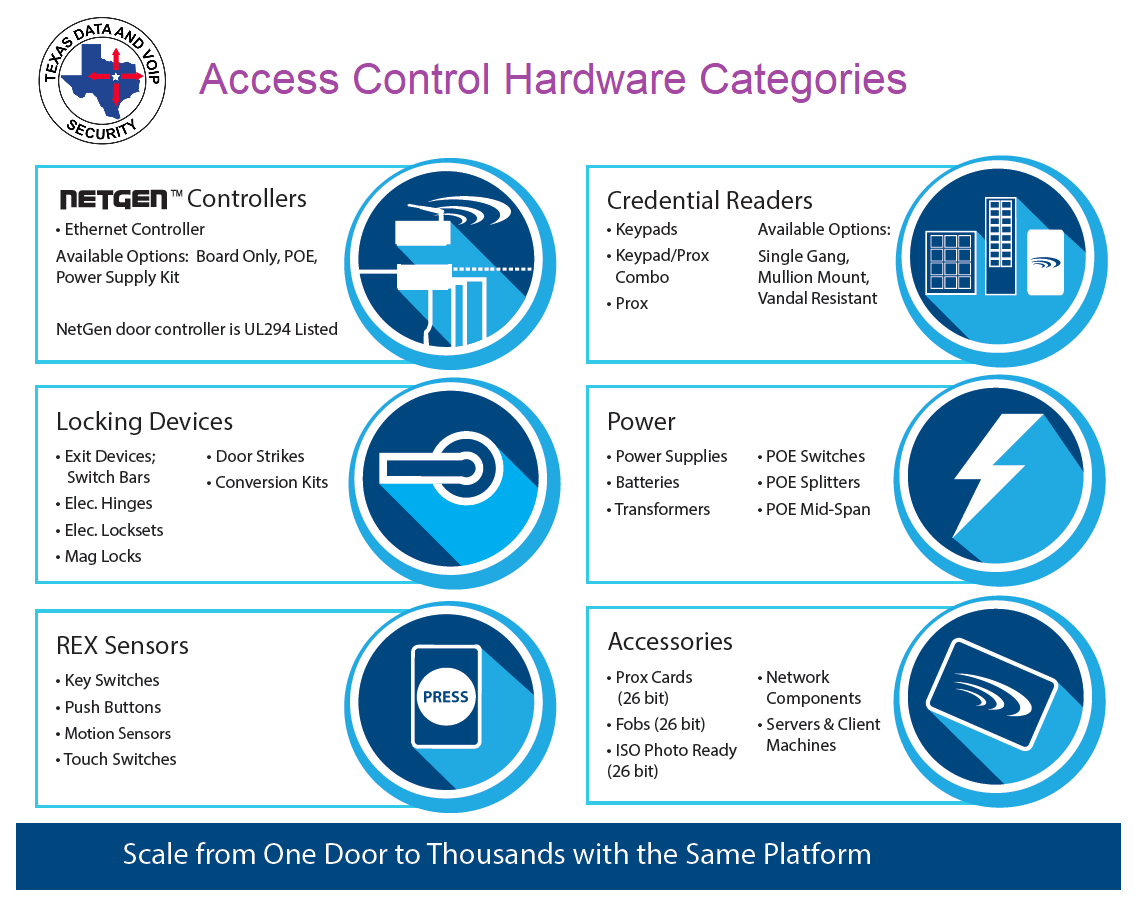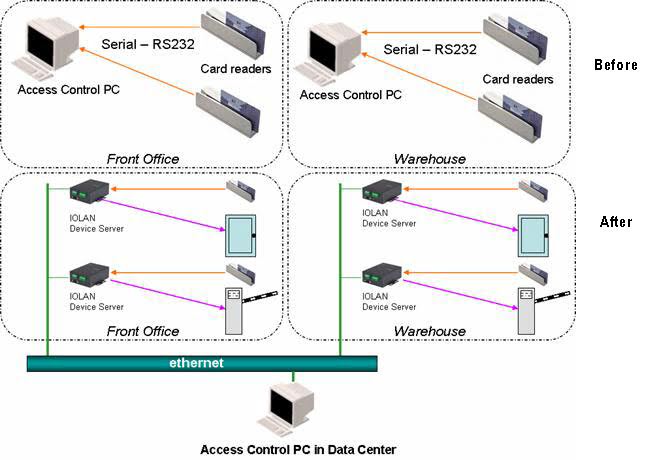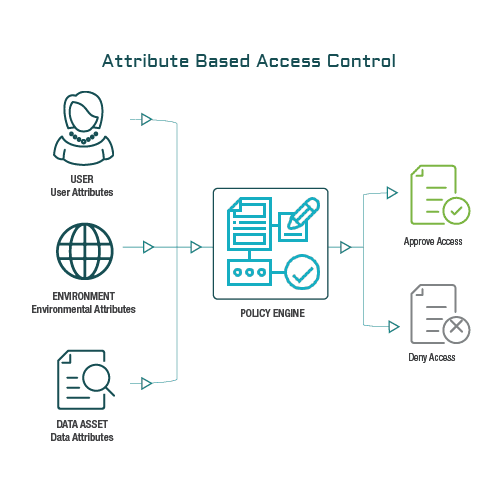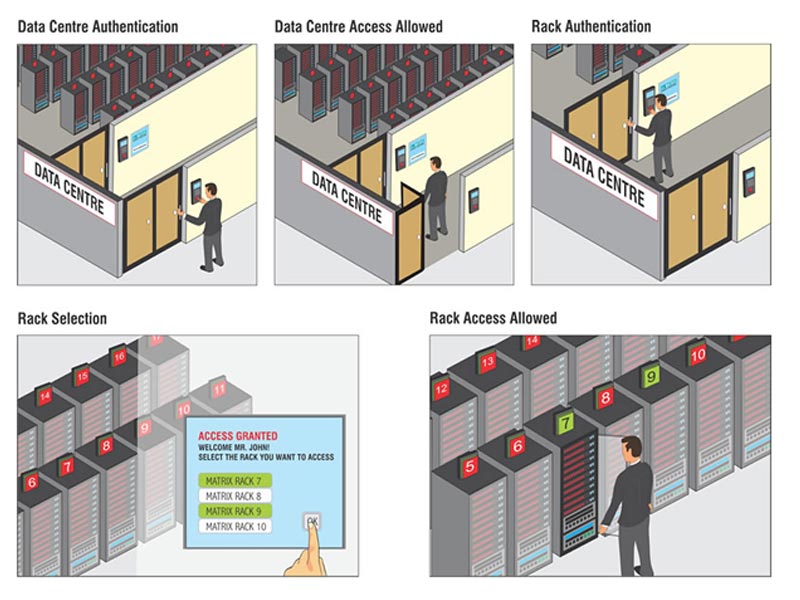
Matrix access control data centre solution | INDUSTRIAL SAFETY REVIEW | Fire Industry Magazine | Safety Magazine India | Security Magazine India | Life Safety Magazine | Occupational Health Safety Magazine

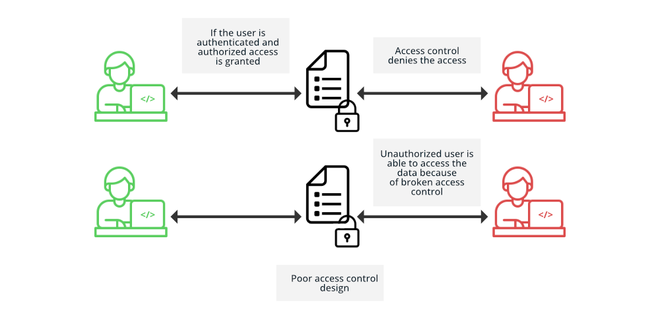
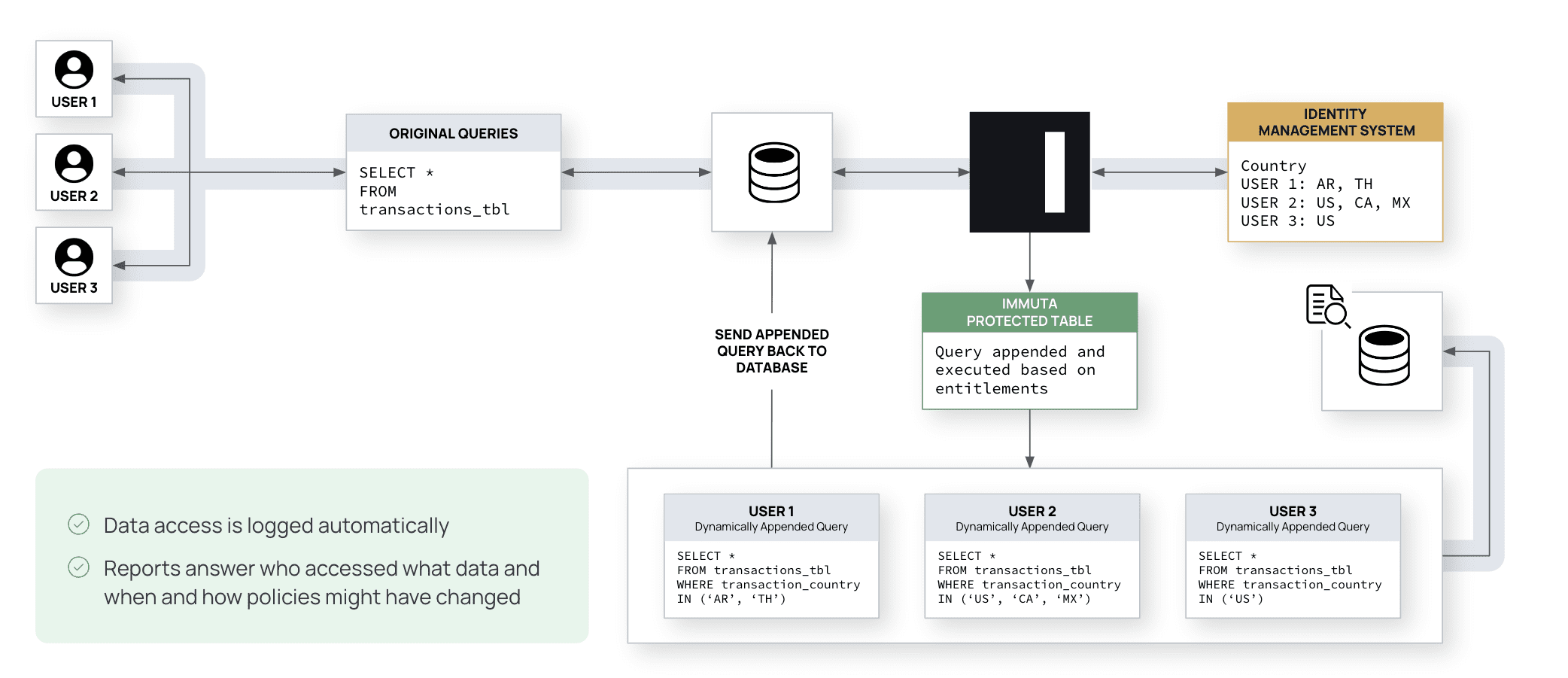
Build a centralized granular access control to manage assets and data access in Amazon QuickSight | AWS Big Data Blog